Home /
Expert Answers /
Computer Science /
suppose-nodes-d-e-and-t-of-the-exabyte-problem-represent-computers-in-a-secure-environment-if-no-d-pa979
(Solved): Suppose nodes d, e and t of the ExaByte problem represent computers in a secure environment. If no d ...
Suppose nodes d, e and t of the ExaByte problem represent computers in a secure environment. If no data is allowed to leave this secure environment, what will the new data transfer model be? Solve this new model and compare ???????the optimal solution to the optimal solution to the original model.
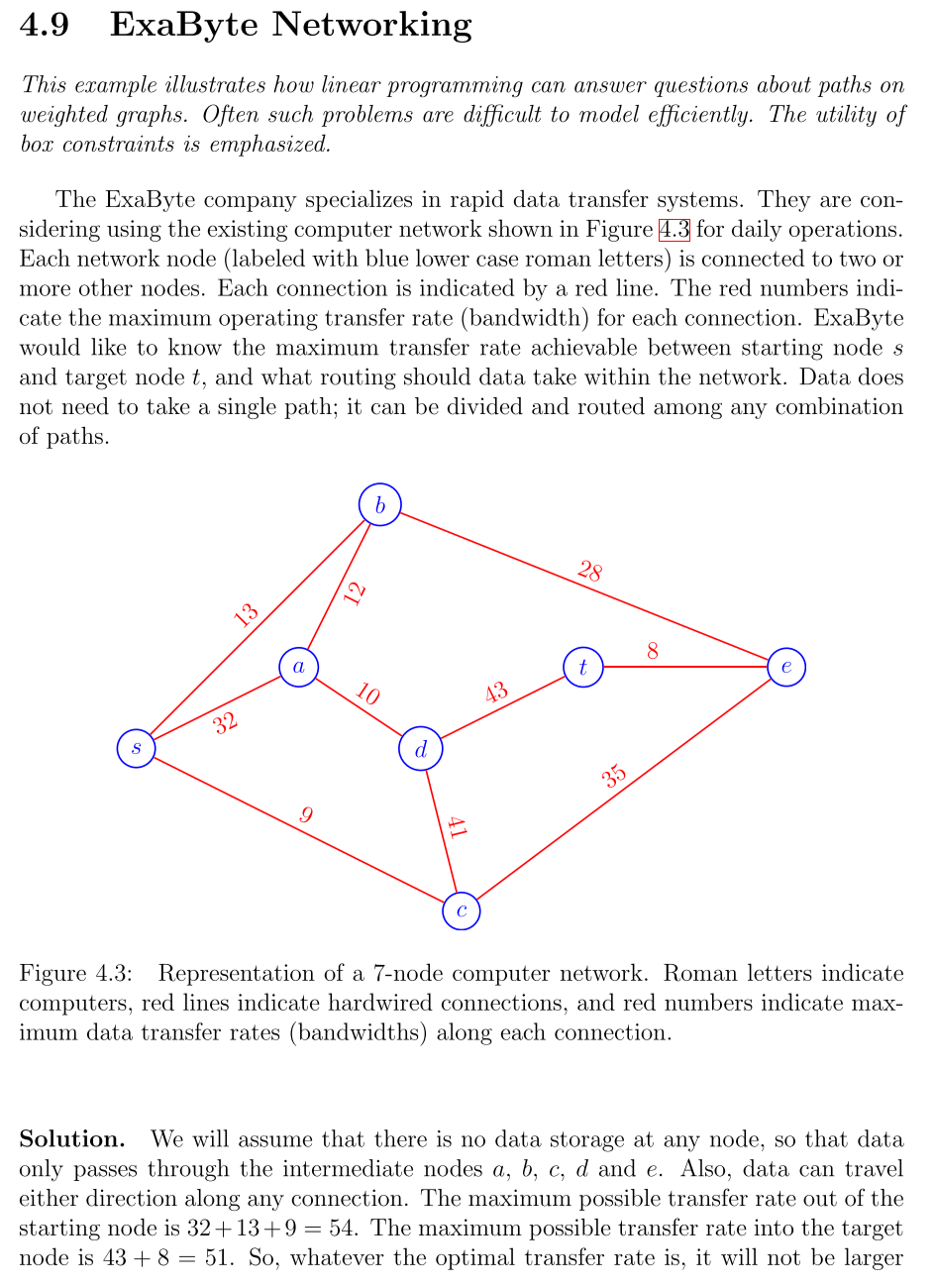
4.9 ExaByte Networking This example illustrates how linear programming can answer questions about paths on weighted graphs. Often such problems are difficult to model efficiently. The utility of box constraints is emphasized. The ExaByte company specializes in rapid data transfer systems. They are considering using the existing computer network shown in Figure for daily operations. Each network node (labeled with blue lower case roman letters) is connected to two or more other nodes. Each connection is indicated by a red line. The red numbers indicate the maximum operating transfer rate (bandwidth) for each connection. ExaByte would like to know the maximum transfer rate achievable between starting node and target node , and what routing should data take within the network. Data does not need to take a single path; it can be divided and routed among any combination of paths. Figure 4.3: Representation of a 7-node computer network. Roman letters indicate computers, red lines indicate hardwired connections, and red numbers indicate maximum data transfer rates (bandwidths) along each connection. Solution. We will assume that there is no data storage at any node, so that data only passes through the intermediate nodes and . Also, data can travel either direction along any connection. The maximum possible transfer rate out of the starting node is . The maximum possible transfer rate into the target node is . So, whatever the optimal transfer rate is, it will not be larger
than 51 . It remains to be seen whether or not the network can support an overall transfer rate of 51 . We choose decision variables which measure the data transfer rate used along each network connection. Let where and are taken from the node set . In particular, we have the 10 decision variables Each decision variable can take on positive or negative values with the meaning: The objective is to maximize the transfer rate from node to node . But as we have already seen, this can be measured by maximizing the transfer rate either out of node or into node . If we choose the latter, we have Flow along each connection is limited by the connection bandwidth. For example, the connection between node and node has a bandwidth of 12 , so we have the constraints Since we need not consider data transfer into the starting node we have And, since we need not consider data transfer out of the target node we have Taken all together, we have the box constraints on bandwidth
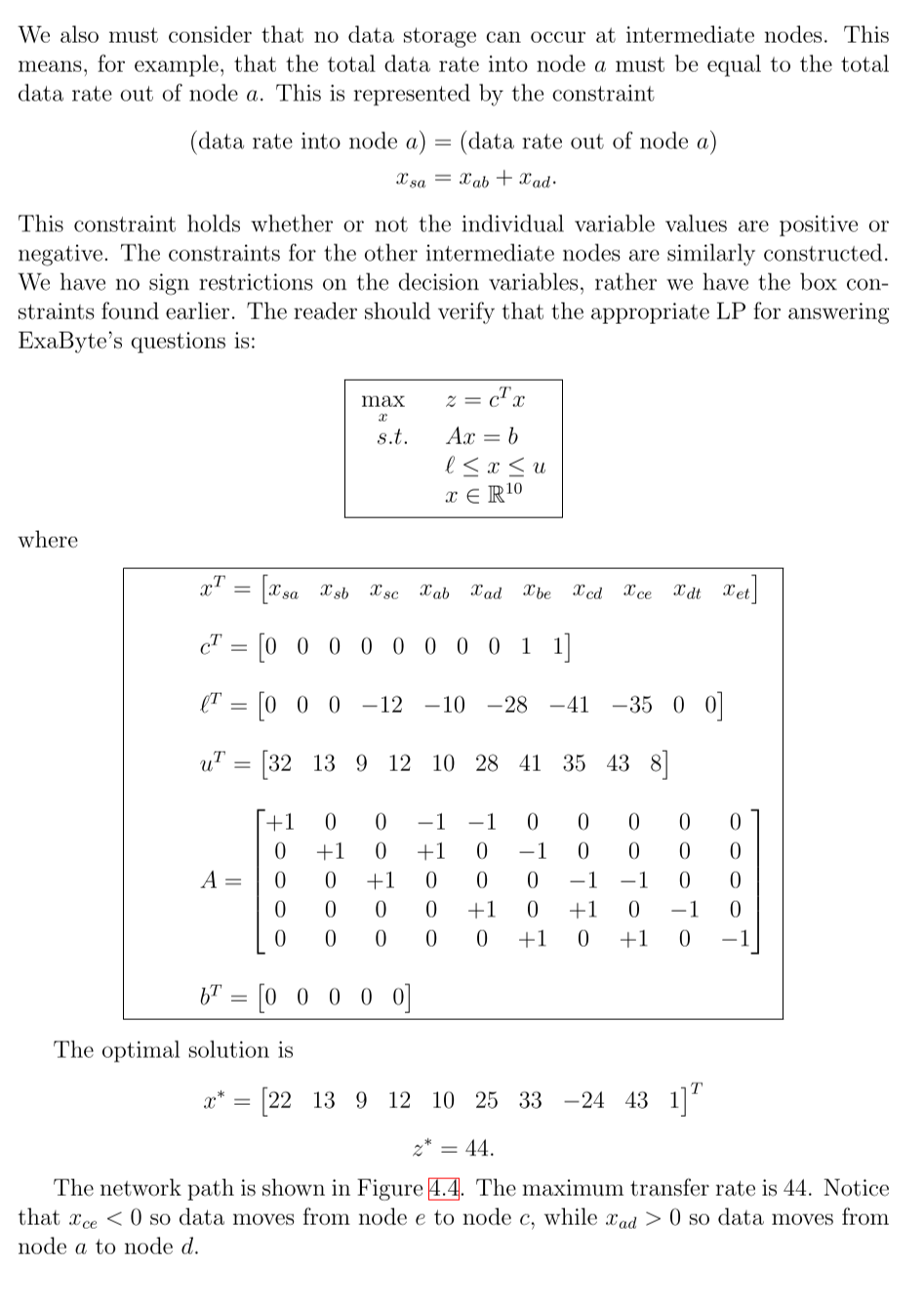
We also must consider that no data storage can occur at intermediate nodes. This means, for example, that the total data rate into node a must be equal to the total data rate out of node . This is represented by the constraint This constraint holds whether or not the individual variable values are positive or negative. The constraints for the other intermediate nodes are similarly constructed. We have no sign restrictions on the decision variables, rather we have the box constraints found earlier. The reader should verify that the appropriate LP for answering ExaByte's questions is: where The optimal solution is The network path is shown in Figure 4.4. The maximum transfer rate is 44. Notice that so data moves from node to node , while so data moves from node to node .
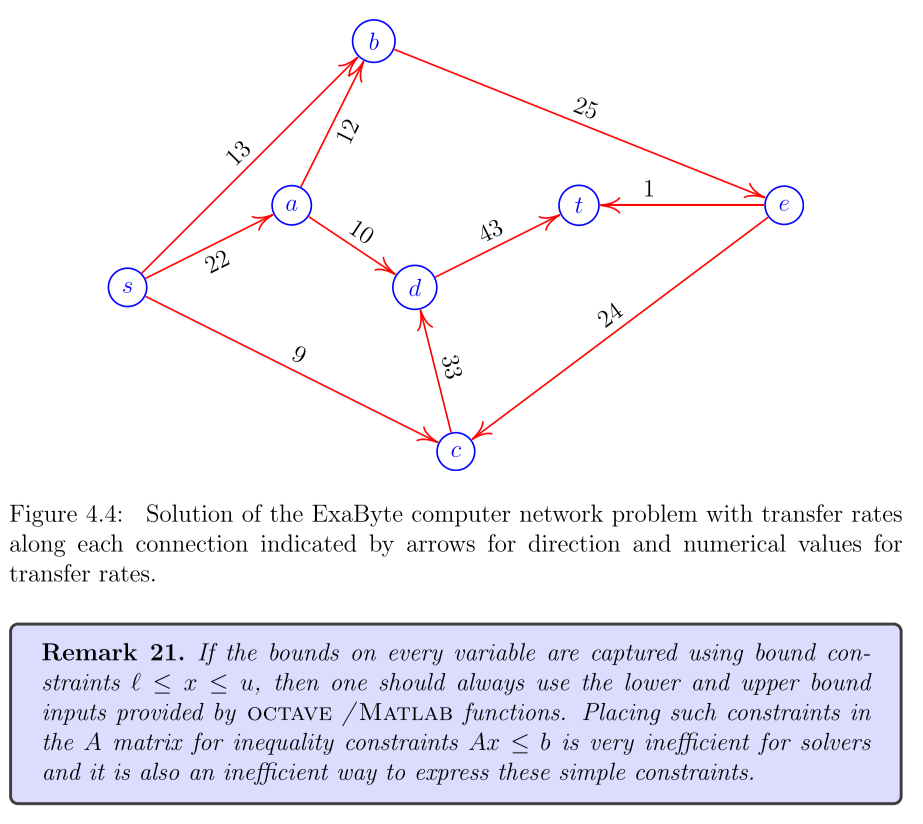
Figure 4.4: Solution of the ExaByte computer network problem with transfer rates along each connection indicated by arrows for direction and numerical values for transfer rates. Remark 21. If the bounds on every variable are captured using bound constraints , then one should always use the lower and upper bound inputs provided by OCtave /Matlab functions. Placing such constraints in the A matrix for inequality constraints is very inefficient for solvers and it is also an inefficient way to express these simple constraints.
Expert Answer
In the original ExaByte problem, we assume that any node can transfer data to any other node, regardless of whether they are in the same secure enviro